Cluster Access
-
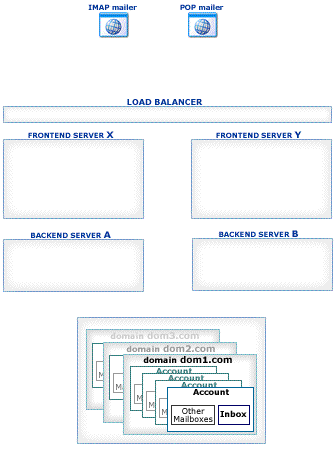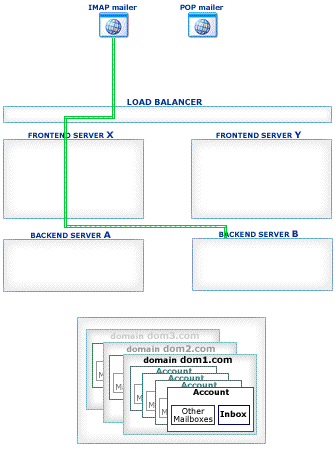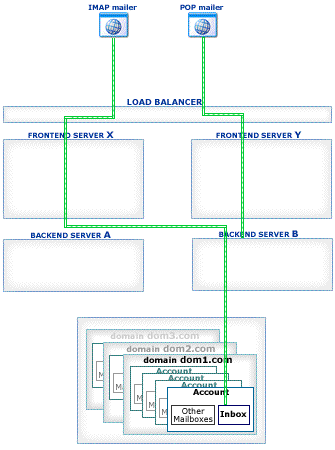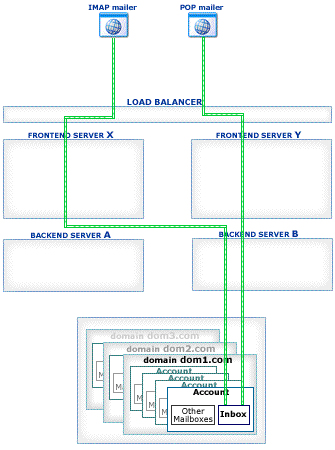
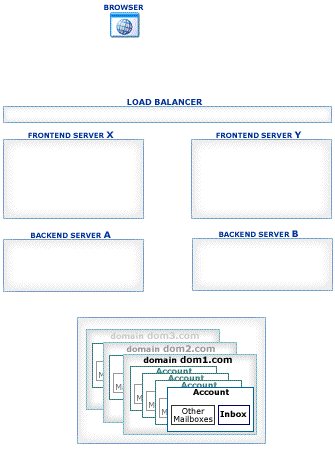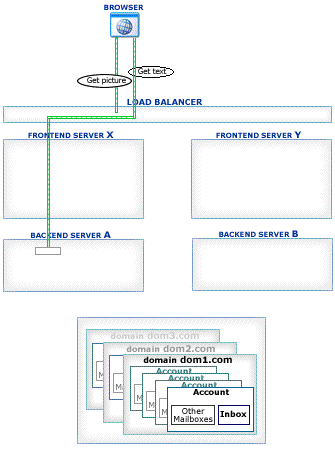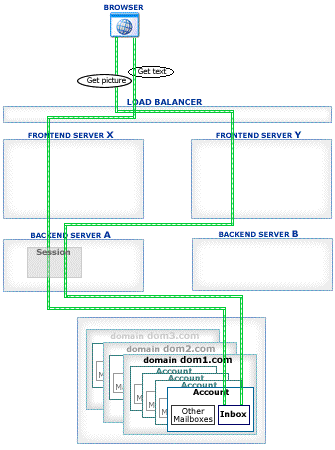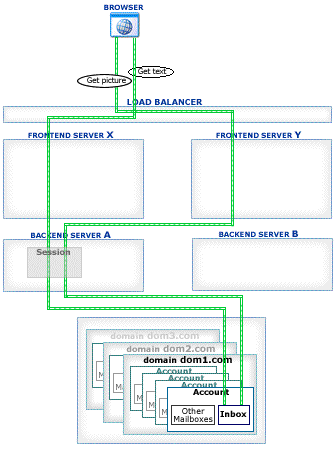
This section explains how Account Access operations work in the CommuniGate Pro Cluster environment.
The CommuniGate Pro Cluster architecture allows a load balancer to direct any connection to any working Server, eliminating a need for complex and unreliable "high-level" load balancer solutions. Inexpensive Layer 4 Switches can be used to handle the traffic.