The "original, "basic" SIP communication model assumes that endpoints can communicate directly,
i.e. that all "elements", including SIP clients - phones, softphones, PBX applications), and SIP servers
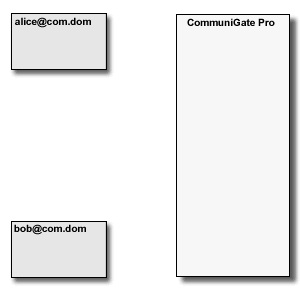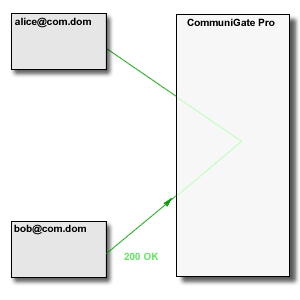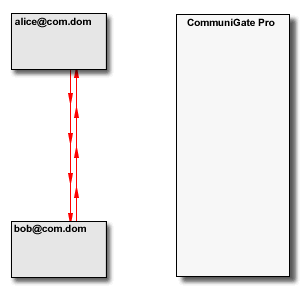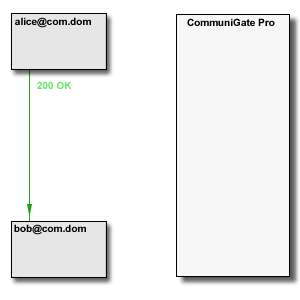
have "real" Internet IP Addresses. In this situation the Server (SIP Proxy) is needed only to
establish a call. Media data and in-call signalling requests are sent directly between the endpoints:
CommuniGate Pro supports automatic "NAT traversal" for the standard-based
real-time communications.
Near-End NAT Traversal
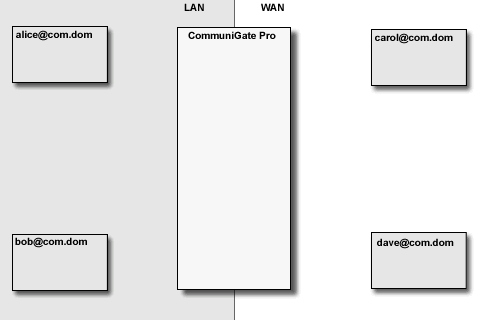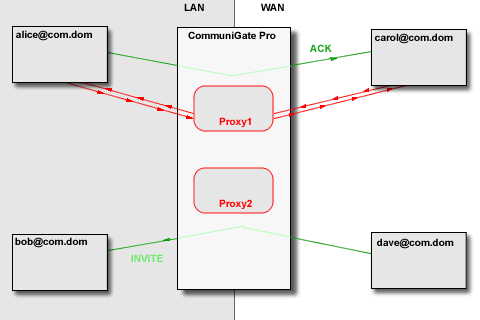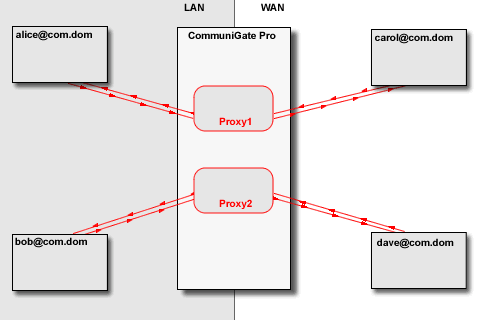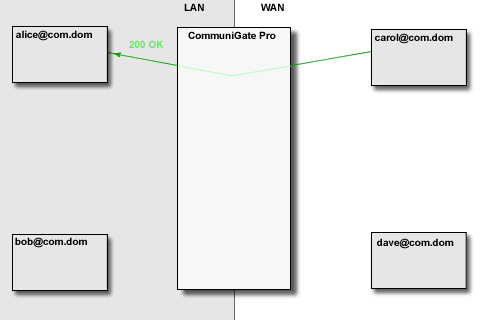
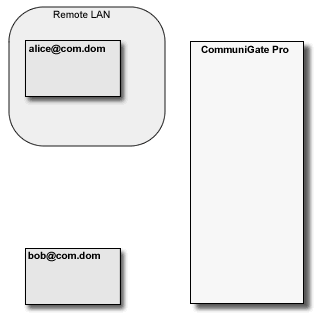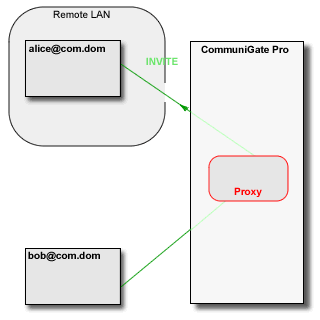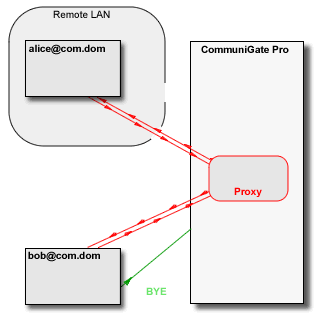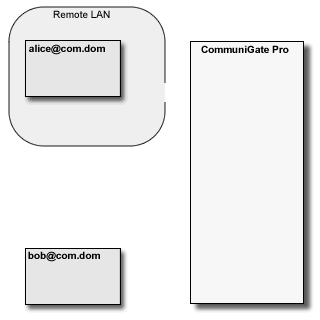
The CommuniGate Pro SIP Module detects the session initiation requests
that are sent from one side of NAT to the other side (a request from a LAN client to a party
on the Internet/WAN and vice versa). In this case, the Server uses some local server port (or a set of ports
depending on the media protocol(s) used) to build a media stream proxy. The Server then modifies the
session initiation request to direct the traffic from both sides to that proxy.
The media proxy relays media data between the "LAN leg" and the "WAN leg" of the media connection:
The CommuniGate Pro SIP Module detects session re-INVITE requests as well as BYE requests and
update and removes the session proxies accordingly. The time-out mechanism is used to remove "abandoned" media proxies.
The CommuniGate Pro provides NAT proxy services for:
- UDP media protocols
- RTP media protocols based on UDP
- TCP media protocols
- T.120 media protocols based on TCP
Note: If you need the Media Stream Proxy functionality, make sure that the LAN and NAT data is
specified correctly on the LAN IPs settings page.
Far-End NAT Traversal
The CommuniGate Pro SIP Module also provides the "far-end" NAT traversal capabilities by detecting requests
coming from clients located behind remote Firewall/NATs.
The Module adds appropriate Record-Route and Path headers to these requests and it builds
media proxies to relay traffic to and from those clients.
Note: modern SIP clients support various NAT traversal methods (STUN, etc.).
Many of these implementations are quite buggy, so it is often more reliable to switch the client-side
NAT traversal methods off, and rely on the CommuniGate Pro SIP Module far-end NAT traversal capabilities instead.
Note: due to the nature of the TCP protocol and the Firewall concept,
it is not possible (in general) to open a TCP connection to a client behind a far-end NAT
("near-end" NAT configurations do not have this problem). This means that clients behind a far-end NAT
cannot initiate TCP (T.120) sessions.
To solve this problem, you may want to:
- always initiate TCP sessions from a client that is not behind a far-end NAT/Firewall
(these clients accept those invitations and start outgoing TCP connections without a problem)
or
- use an additional copy of the CommuniGate Pro Server on that remote location
as a near-end NAT traversal solution for that network, eliminating a need for far-end NAT traversal on the "main" CommuniGate Pro server
or
- configure the remote Firewall/NAT to relay all incoming TCP request to the T.120 port (usually, the port 1503) to
a particular workstation behind that Firewall.
Edge Services
The CommuniGate Pro SIP Module can be used as an "Edge Service" or ALG ("Application Level Gateway"),
providing NAT traversal functionality for users registered on other servers.
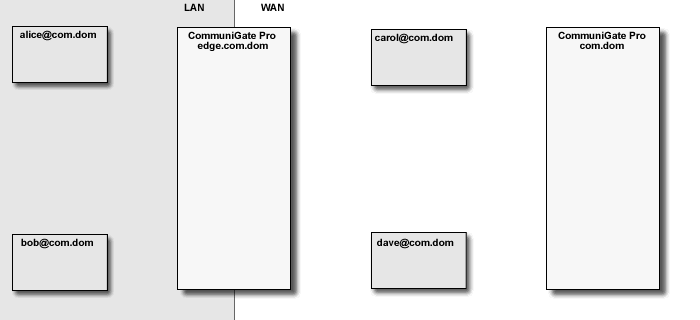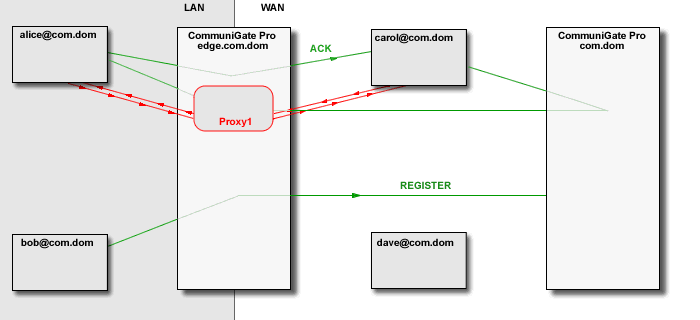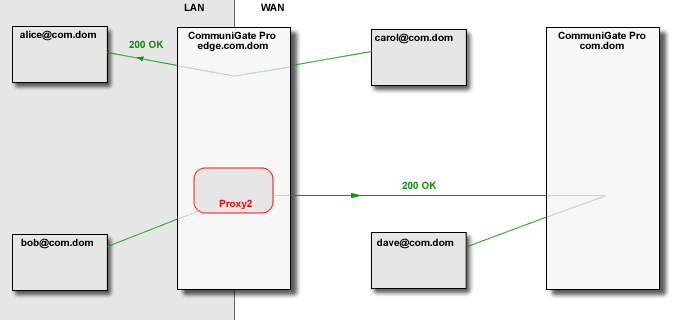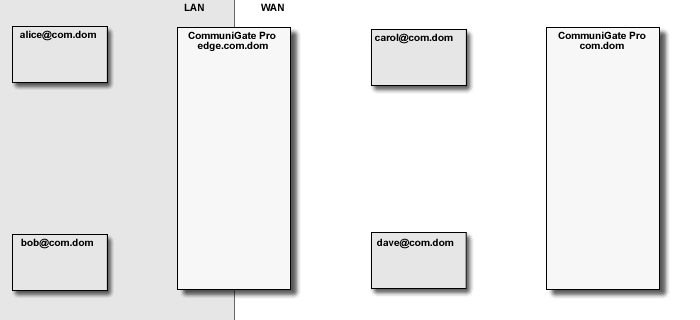
The CommuniGate Pro SIP Module detects "media loops", when a call placed from within LAN is proxied
to WAN, and then proxied back to the same LAN. In this case the Media Proxies are removed, eliminating
unnecessary overhead, and allowing SIP clients to communicate directly within one LAN, while proving
registrar services outside that LAN.
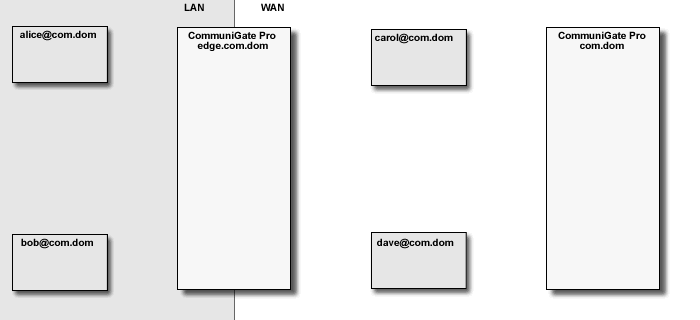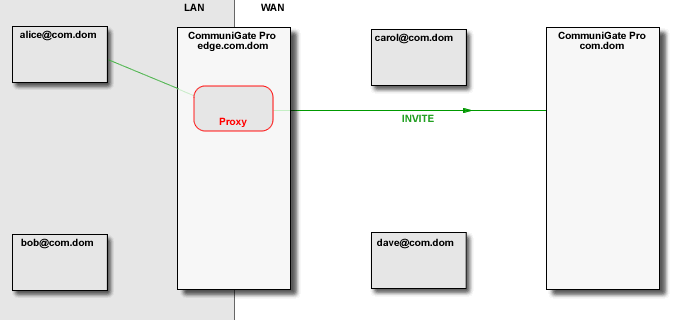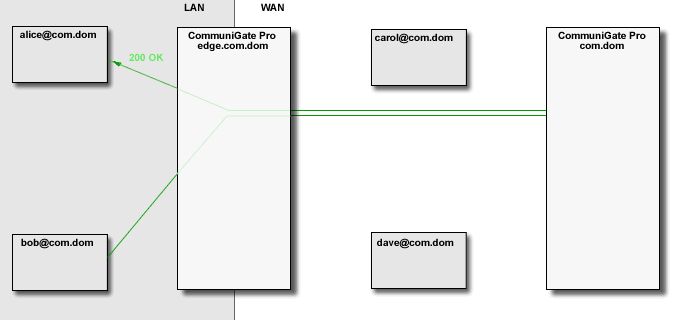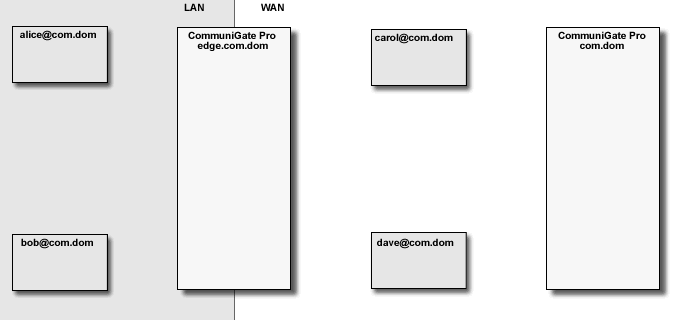
The SIP module can detect much more complex loop cases, either avoiding Media Proxies altogether, or
minimizing the number of Media Proxies used.




